How to set up a VPN Site to Site (VPN S2S) between StrongSwan and Cloud VPN
Requirement
- GCP Console
- VM with Ubuntu 22.04 or CentOS
- VM Directly Connected to IP Public, or
- VM Behind NAT, & these port must be forwarded : UDP port 500, UDP port 4500, and allow ESP packets
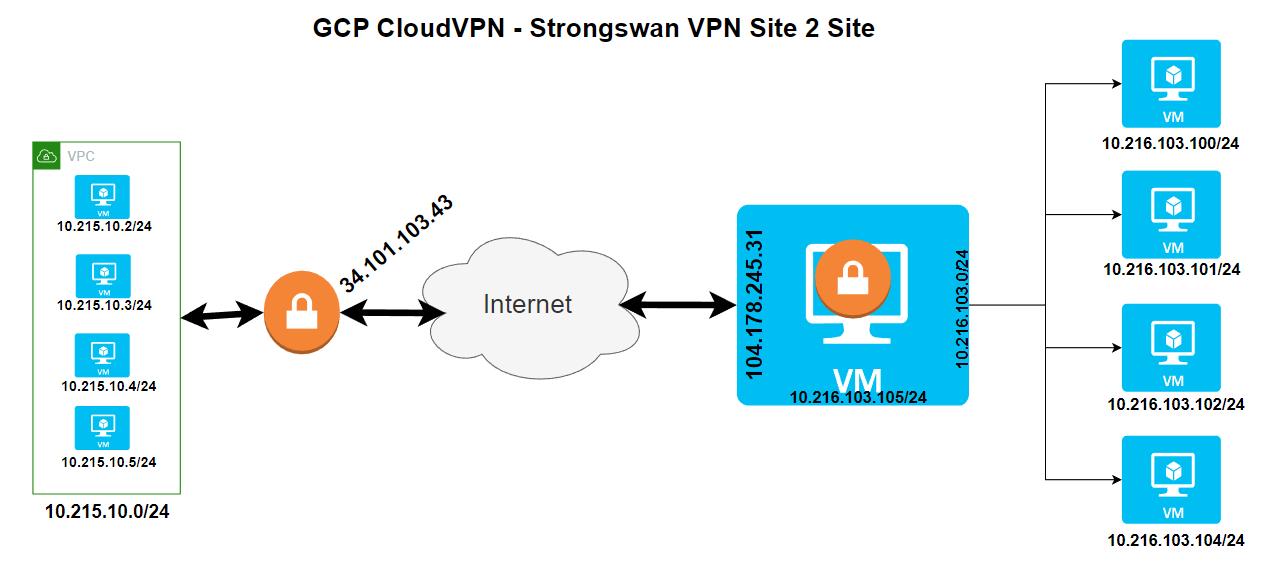
Topology
VPN Parameter
IPsec parameters
Cloud VPN supports an extensive list of ciphers that can be used per your security policies. The following parameters and values are used in the Gateway’s IPsec configuration for the purpose of this guide.
| Parameter | Value |
|---|---|
| IPsec Mode | Tunnel mode |
| Auth protocol | Pre-shared-key |
| Key Exchange | IKEv2 |
| Start | Auto |
| Perfect Forward Secrecy (PFS) | on |
These are the Cipher configuration settings for IKE phase 1 and phase 2 that are used in this guide.
| Phase | Cipher role | Cipher |
|---|---|---|
| Phase-1 | Encryption | aes256 |
| (ike) | Integrity | sha1 |
| Diffie-Helman | modp1024 |
|
| Phase1 lifetime | 28800 | |
| Phase-2 | Encryption | aes256 |
| (esp) | Integrity | sha1 |
| Diffie-Helman | modp1024 |
|
| Phase2 lifetime | 3600 |
Configuring policy-based IPsec VPN
Below is a sample environment to walk you through the setup of a policy-based VPN. Make sure to replace the IP addresses in the sample environment with your own IP addresses.
Cloud VPN
| Name | Value |
|---|---|
| Cloud VPN(external IP) | 34.101.103.43 |
| VPC CIDR | 10.215.10.0/24 |
strongSwan
| Name | Value |
|---|---|
| External IP | 104.178.245.31 |
| CIDR Behind strongSwan | 10.216.103.0/24 |
Configuration of Google Cloud
To configure Cloud VPN:
In the Cloud Console, select Networking > Create VPN connection.
Click CREATE VPN CONNECTION.
Populate the fields for the gateway and tunnel as shown in the following table, and click Create:
| Parameter | Value | Description |
|---|---|---|
| Name | gcp-to-strongswan-1 |
Name of the VPN gateway. |
| Description | VPN tunnel connection between GCP and strongSwan |
Description of the VPN connection. |
| Network | to-sw |
The Google Cloud network the VPN gateway attaches to. This network will get VPN connectivity. |
| Region | europe-west4 |
The home region of the VPN gateway. Make sure the VPN gateway is in the same region as the subnetworks it is connecting to. |
| IP address | gcp-to-strongswan(34.101.103.43) |
The VPN gateway uses the static public IP address. An existing, unused, static public IP address within the project can be assigned, or a new one created. |
| Remote peer IP address | 104.178.245.31 | Public IP address of the on-premises VPN appliance used to connect to the Cloud VPN. |
| IKE version | IKEv2 |
The IKE protocol version. You can select IKEv1 or IKEv2. |
| Shared secret | RSgu90cStYM60GnE8YajIVnRebRjHQOQ | A shared secret used for authentication by the VPN gateways. Configure the on-premises VPN gateway tunnel entry with the same shared secret. |
| Routing options | Policy-based |
Multiple routing options for the exchange of route information between the VPN gateways. This example uses static routing. |
| Remote network IP ranges | 10.215.10.0/24 | The on-premises CIDR blocks connecting to Google Cloud from the VPN gateway. |
| Local IP ranges | 10.216.103.0/24 | The Google Cloud IP ranges matching the selected subnet. |
StrongSwan Setup
Installation of StrongSwan
Configure the kernel to enable packet forwarding for IPv4. Edit the configuration file
Add the following lines at the end of the file.
Save and exit the file then run the following command to load settings.
Install strongSwan and supporting dependencies:
Set the service to start on boot.
Check for the service status
Configure IPSEC Preshared Key
Add the Key to /etc/ipsec.secrets file
Add the key:
the syntax is : <peer IP> : PSK “preshared key”
Save and exit the file.
Configure IPSEC conf File
Make a copy of the configuration file then set up the VPN configuration on that file.
Add the following details to the file.
Save and exit the file.
Glosary
- config setup specifies general configuration information for IPSec which applies to all connections.
- charondebug = “all” defines how much Charon debugging output should be logged.
- uniqueids = yes states whether a particular participant ID should be kept unique.
- conn SiteA-SiteB is the connection name.
- authby=secret specifies how the connection is authenticated.
- auto=start allows the connection to start by default.
- type=tunnel is the type of connection.
- left=138.201.255.67 is the public IP address of server A.
- leftsubnet=192.168.200.43/24 is the subnet/private IP of server A.
- right=95.217.16.14 is the public IP address of server B/remote server.
- rightsubnet=192.168.200.130/24 is the subnet/private IP of server B.
- ike=aes256-sha1-modp1024 is the type of encryption when the Internet key exchange.
- keyexchange=ikev2 is the Internet key exchange version.
- ikelifetime=28800s is the time before the re-authentication of keys.
- esp=aes256-sha1! is the encapsulation security suite of protocols.
- aggressive states whether to use Aggressive or Main Mode.
- keyingtries states the number of attempts that should be made to negotiate a connection.
- lifetime defines how long a particular instance of a connection should last, from successful negotiation to expiry.
- dpddelay specifies the time interval with which exchanges are sent to the peer.
- dpdtimeout specifies the timeout interval to delete connections in case of inactivity.
- dpdaction states how to use the Dead Peer Detection(DPD) protocol to manage the connection.
If you have an active firewall, configure it to add the rules
Restart the VPN
You can start and stop IPsec with the following command
Test connection from both side, if you still cannot reach GCP side from Strongswan side, try open/ setup Firewall in GCP








top
Thanks for thr great article!
Thanks for thr great article!
I am not real superb with English but I line up this very easygoing to read.
Thank you so much!